Year in Review: Cyber Threats by the Numbers
The report shows a complex and getting more complex cyber threat environment:
87,400 cybercrime reports in FY2023–24, one every six minutes. Although that’s a 7% decrease, it’s still a big number.
36,700 calls to the Australian Cyber Security Hotline, an average of 100 calls per day, up 12% from last year.
Self reported cost of cybercrime for individuals up 17% to an average of $30,700 per report.
Business email compromise (BEC) still the biggest problem, $84 million lost, with an average of $55,000 lost per confirmed incident.
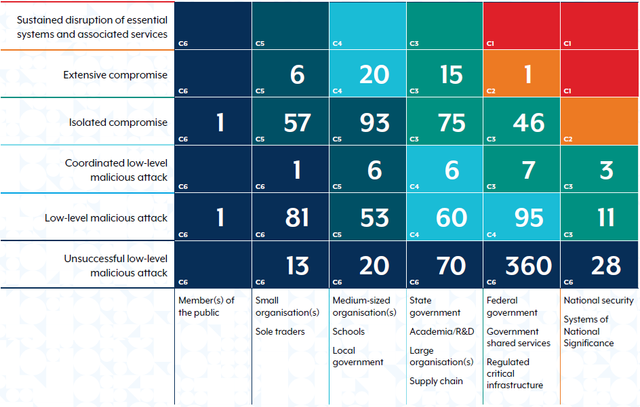
Critical Infrastructure: A Big Target
Critical infrastructure is a prime target for cyber attackers because of the services it provides and the data it holds. The ASD said:
11% of cyber incidents responded to in FY2023–24 were against critical infrastructure.
Top tactics were phishing (23%), public facing applications (21%) and brute force (15%).
DoS and DDoS attacks were over represented in these incidents, twice as many as other sectors.
The impact of attacks on critical infrastructure is far reaching, affecting the economy, national security and everyday Australians. Malicious actors – from state sponsored groups to cybercriminals – are exploiting vulnerabilities in interconnected operational technology (OT) and information technology (IT) systems.
State Sponsored Threats: The Smarter Actors
The report highlights the ongoing threat from state sponsored actors:
China and Russia are named as the primary threats, with Chinese actors using “living off the land” (LOTL) to maintain persistent access to critical infrastructure. This means disguising malicious activity as normal network behaviour.
Russia’s use of adaptive techniques such as cloud exploitation shows the state sponsored tradecraft is getting smarter.
Phishing tools are still common and effective, as seen in spear phishing campaigns from Russian actors targeting governments and academia globally.
The ASD also worked with international partners to release joint advisories on these threats and mitigations for organisations.
Cybercrime Trends: AI Driven Threats and Ransomware
Cybercriminals are innovating fast:
The rise of artificial intelligence (AI) is allowing low sophistication actors to launch more targeted attacks, including AI generated phishing and deepfakes.
A notable example was vishing (video phishing) where a multinational was tricked into transferring millions of dollars using an AI generated deepfake video call.
Ransomware is still a big problem, 11% of all incidents. Malicious actors are now using data theft extortion, where sensitive information is stolen and used to extort victims without encrypting systems.
Despite improved cyber defences the report says don’t pay the ransom as it feeds the cyber criminal business model.
Resilience and Response: National
The Australian Government is investing more in cybersecurity:
Under the 2024 Integrated Investment Program $15–$20 billion has been allocated to cyber capabilities, including offensive operations and infrastructure protection.
Autonomous cyber sanctions were used for the first time against two Russian cybercriminals involved in ransomware attacks, a tougher approach to cybercrime.
The report also notes the importance of partnerships:
Over 119,300 organisations are part of the ASD Cyber Security Partnership Program.
The Cyber Threat Intelligence Sharing (CTIS) platform allows real time, bidirectional sharing, faster and more scale.
How to Strengthen Your Defences
The report recommends proactive action to counter the threats. Here are the key recommendations:
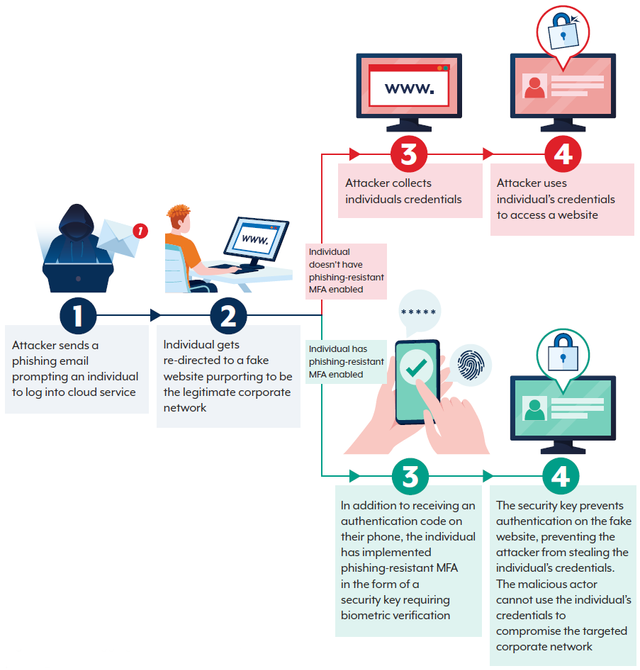
MFA: Simple and effective defence against unauthorised access.
Software Updates: Keep systems patched.
Network Segmentation: Isolate critical systems in case of a breach.
Incident Response Plans: Assume a breach will happen and plan for it.
Secure Supply Chains: Vet vendors before integrating their products or services.
Get Involved
The 2023–2024 Cyber Threat Report is not just a report, it’s a call to action. Whether you’re an individual, a business or a government agency, being vigilant and investing in good cyber practices is no longer a nice to have, it’s a must.
Discussions and Comments
Click here to view and join in on any discussions and comments on this article.

